- Executando varredura simples:
msf > use auxiliary/scanner/portscan/tcp
msf auxiliary(tcp) > set RHOSTS 192.168.1.108
RHOSTS => 192.168.1.108
msf auxiliary(tcp) > set PORTS 1-4000
PORTS => 1-4000
msf auxiliary(tcp) > set THREADS 30
THREADS => 30
msf auxiliary(tcp) > run
[*] 192.168.1.108:23 - TCP OPEN
[*] 192.168.1.108:25 - TCP OPEN
[*] 192.168.1.108:22 - TCP OPEN
[*] 192.168.1.108:21 - TCP OPEN
[*] 192.168.1.108:53 - TCP OPEN
[*] 192.168.1.108:80 - TCP OPEN
[*] 192.168.1.108:139 - TCP OPEN
[*] 192.168.1.108:445 - TCP OPEN
[*] 192.168.1.108:3306 - TCP OPEN
[*] 192.168.1.108:3632 - TCP OPEN
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Bem, vamos explicar:
primeiramente utilizado o módulo de scan TCP, setamos o host alvo através do comando set rhosts, setamos as portas de 1 até 4000, pois a varredura de 65535 portas não é necessário aqui, setamos threads , ou seja, concorrência em 30, vale ressaltar que devemos tomar cuidado, pois podem haver impactos no ambiente, por fim executamos a varredura através do comando run. Caso tenha dúvidas lembre-se que você pode utilizar o comando show options:
msf auxiliary(tcp) > show options
Module options (auxiliary/scanner/portscan/tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
CONCURRENCY 10 yes The number of concurrent ports to check per host
FILTER no The filter string for capturing traffic
INTERFACE no The name of the interface
PCAPFILE no The name of the PCAP capture file to process
PORTS 1-4000 yes Ports to scan (e.g. 22-25,80,110-900)
RHOSTS 192.168.1.108 yes The target address range or CIDR identifier
SNAPLEN 65535 yes The number of bytes to capture
THREADS 30 yes The number of concurrent threads
TIMEOUT 1000 yes The socket connect timeout in milliseconds
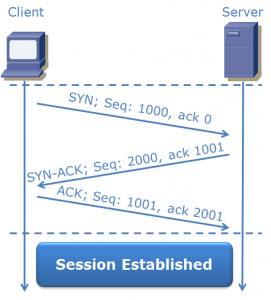
Bem, a varredura TCP trabalha com a técnica TCP Connect() ou seja, Three-way Handshake (Handshake de três vias) , torna-se de fácil detecção.
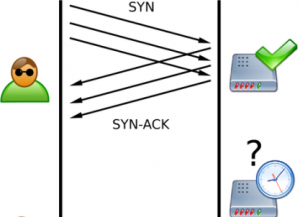
Diante disso vamos utilizar a técnica Syn ou Half Open, meia conexão, pois não completa o Three-way.
msf > use auxiliary/scanner/portscan/syn
msf auxiliary(syn) > show options
Module options (auxiliary/scanner/portscan/syn):
Name Current Setting Required Description
---- --------------- -------- -----------
BATCHSIZE 256 yes The number of hosts to scan per set
INTERFACE no The name of the interface
PORTS 1-10000 yes Ports to scan (e.g. 22-25,80,110-900)
RHOSTS yes The target address range or CIDR identifier
SNAPLEN 65535 yes The number of bytes to capture
THREADS 1 yes The number of concurrent threads
TIMEOUT 500 yes The reply read timeout in milliseconds
msf auxiliary(syn) > set RHOSTS 192.168.1.108
RHOSTS => 192.168.1.108
msf auxiliary(syn) > set PORTS 1-4000
PORTS => 1-4000
msf auxiliary(syn) > set THREADS 30
THREADS => 30
msf auxiliary(syn) > run
[*] TCP OPEN 192.168.1.108:21
[*] TCP OPEN 192.168.1.108:22
[*] TCP OPEN 192.168.1.108:23
[*] TCP OPEN 192.168.1.108:25
[*] TCP OPEN 192.168.1.108:53
[*] TCP OPEN 192.168.1.108:80
[*] TCP OPEN 192.168.1.108:139
[*] TCP OPEN 192.168.1.108:445
[*] TCP OPEN 192.168.1.108:3306
[*] TCP OPEN 192.168.1.108:3632
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Repare que obtivemos o mesmo resultado, porém de forma mais silenciosa.